
Back to Blog
Mastering On-Chain Risk Management in DeFi
A practical guide to on-chain risk management in DeFi. Learn to identify smart contract, oracle, and liquidity risks to protect your crypto assets.
Dec 16, 2025
generated
Jumping into Decentralized Finance (DeFi) without a solid plan is like walking through a minefield blindfolded. That’s where on-chain risk management comes in. It’s the nitty-gritty process of spotting, analyzing, and dealing with threats that live directly on the blockchain. Think of it as the core discipline you need to survive and thrive in DeFi's wild, high-growth world.
Why You Can't Afford to Ignore On-Chain Risk
When you engage with a DeFi protocol, you're putting your capital on the front lines, exposed to a whole new class of dangers you won't find in traditional finance. These aren't just theoretical problems; they're real-world vulnerabilities that have already cost users billions. The very nature of the blockchain—immutable and transparent—means that when things go wrong, the damage is often permanent. Proactive defense isn't just a good idea; it's essential.
The history of DeFi is littered with horror stories. Remember the infamous $625 million Ronin Bridge hack in 2022? Attackers siphoned a fortune from the Axie Infinity network, all because of sloppy private key management. From 2020 to 2024, DeFi exploits have drained over $3.7 billion from protocols, and the attacks are only getting more sophisticated. You can get a sense of where the next threats might come from in this report on emerging risk hotspots. These numbers tell a pretty stark story: risk is baked into the system.
A Pilot's Pre-Flight Checklist
The best way to think about on-chain risk management is like a pilot's pre-flight checklist. Before every single flight, a pilot meticulously runs through every critical system. They don't do this because they expect the plane to fall out of the sky, but because the consequences of failure are catastrophic. That checklist is what gives them the confidence to take off.
In the same way, a strong risk framework in DeFi isn't meant to scare you away from participating. It's about giving you the tools to engage intelligently.
This disciplined approach boils down to a few key activities:
Spotting Threats: Pinpointing potential weaknesses in smart contracts, oracle feeds, and liquidity pools before you put your money in.
Analyzing the Damage: Getting a real sense of the financial fallout if something goes wrong, like a stablecoin de-pegging or a hostile governance takeover.
Mitigating Exposure: Actively taking steps to shield your assets, whether that's diversifying across different protocols or using decentralized insurance.
By treating risk management as a fundamental part of your process, not just an afterthought, you switch from being a passive participant to an empowered investor. This guide is designed to help you build that very checklist.
Ultimately, getting a handle on on-chain risk management is what separates the people who build sustainable wealth in DeFi from those who get wiped out. It gives you the power to protect your capital and confidently chase the incredible opportunities this new financial frontier has to offer.
Mapping the DeFi Risk Landscape
To get a handle on risk, you first need a good map of the terrain. Solid on-chain risk management starts by knowing exactly what dangers you're facing in Decentralized Finance (DeFi). These aren't just vague boogeymen; they're specific, known failure points, each with its own signature and potential to wreck your portfolio.
Think of DeFi as a booming, interconnected city. It’s packed with opportunity, but it also has its share of sketchy neighborhoods and structural weaknesses. By breaking down the risks, we can stop being fearful and start being smart, turning unknown threats into problems we can actually identify and manage.
Smart Contract Risk: The Flawed Blueprint
Every DeFi protocol runs on smart contracts—bits of code that execute transactions all by themselves. This code is basically the protocol's DNA. Smart contract risk is what happens when that code has bugs, loopholes, or vulnerabilities that an attacker can exploit.
It's like building a skyscraper with a faulty blueprint. It doesn't matter how strong your steel is or how good your builders are; a fundamental design flaw can bring the whole thing crashing down. In DeFi, that crash often means every last user fund gets drained in an instant, and there's no getting it back. One recent report showed a staggering 48% jump in crypto fraud in 2024, with much of it targeting these code-level weaknesses.
The key thing to remember: A smart contract's code is law, but a poorly written law can be twisted. An exploit isn't like a bank robbery; it's someone using the contract's own rules against itself to walk away with everything. This is precisely why a professional smart contract security audit is the absolute bare minimum for any protocol you even think about using.
Oracle Risk: The Broken Altimeter
Lots of DeFi protocols, especially lending markets and derivative platforms, need to know what's happening in the real world. They rely on "oracles" to feed them crucial data, like the current price of Ethereum or a stablecoin, to handle liquidations and trades correctly.
Oracle risk is the danger that this outside data is wrong, manipulated, or just too slow. Imagine a pilot flying through a storm who trusts their altimeter completely. If that instrument is broken, they could fly straight into a mountain while thinking they're climbing to safety. In the same way, a lending protocol that gets a manipulated, fake-low price for a collateral asset might fail to liquidate bad debt, quickly spiraling into insolvency.
The diagram below shows how identifying, analyzing, and defending against these varied risks are the pillars of any sound on-chain strategy.
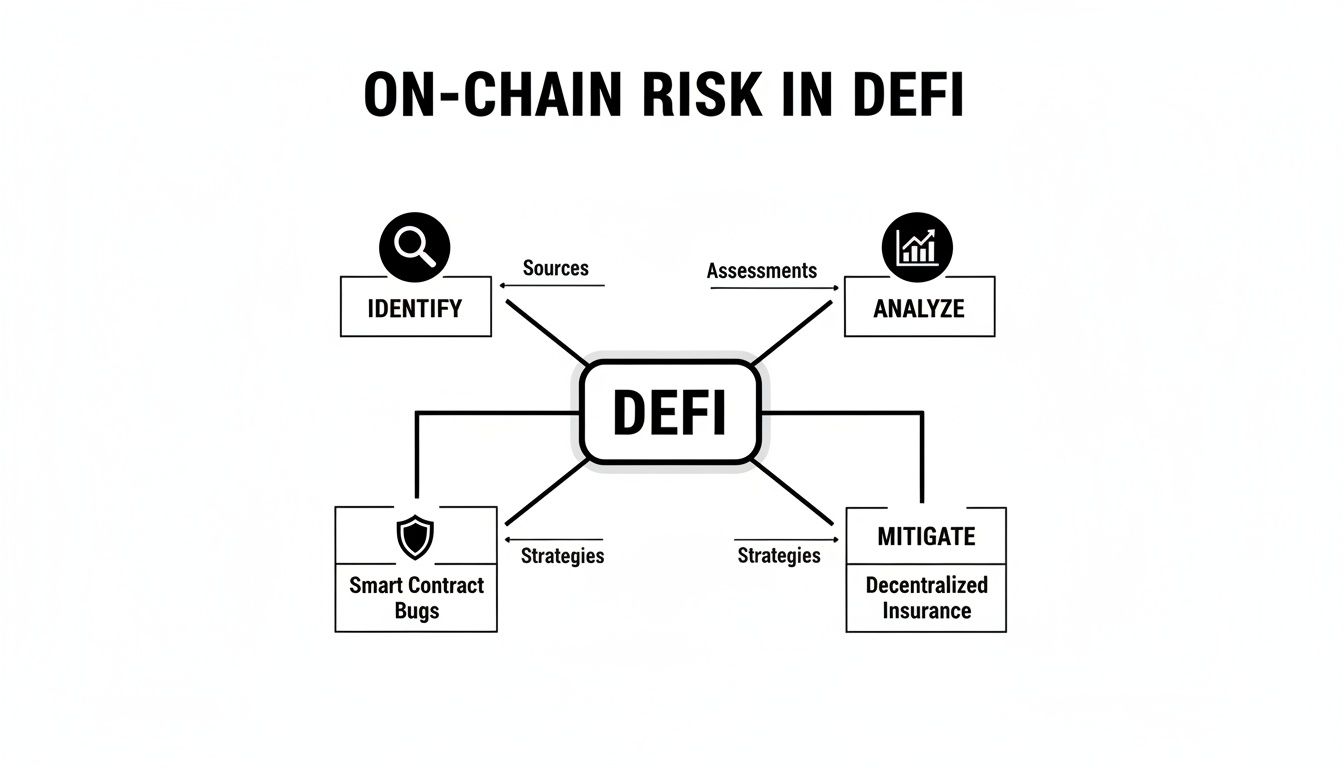
This really drives home the point that risk management isn't a one-and-done task. It's a constant cycle of watching, learning, and adapting your defenses.
Liquidity and Economic Risks
This bucket of risks covers anything that threatens a protocol's financial health and the assets it's built on.
Liquidity Risk: This is the classic "can't sell" problem. It’s the risk of not being able to exit a position without tanking the price. Think of it like owning a priceless painting that nobody actually wants to buy; it's worth a fortune on paper, but you can't turn it into cash. In DeFi, low liquidity can trigger a death spiral of liquidations that bankrupts a protocol.
Composability Risk: DeFi is often called "money legos" because protocols can be stacked on top of each other. This is awesome for innovation, but it also creates a massive domino effect. If one of the foundational "lego" protocols breaks, it can set off a chain reaction that topples everything built on top of it.
Counterparty Risk: At its core, this is the risk that someone else in a deal won't hold up their end of the bargain. In DeFi, this often points to risks with bridges (which connect different blockchains) or the collateral backing an asset. Getting a grip on understanding stablecoin risks is non-negotiable here, as the failure of a stablecoin's backing can send shockwaves across the entire ecosystem.
The Sneakier On-Chain Threats
Beyond the obvious technical and economic dangers, there are more subtle threats lurking in the shadows. These are less about breaking code and more about bending the rules of the game.
MEV (Maximal Extractable Value) is the profit that block builders can skim by reordering, inserting, or even censoring your transactions. It's like a stock exchange clerk seeing your big "buy" order coming and sneaking in their own order milliseconds before yours to profit from the price jump you're about to cause.
Governance Risk pops up when a protocol’s voting system gets hijacked. A bad actor could buy up enough governance tokens to pass a vote that lets them drain the treasury or rewrite the rules to their own benefit.
To give you a clearer picture, here’s a quick breakdown of the major risk categories and your first line of defense against them.
A Snapshot of Key On-Chain Risks and Defenses
Risk Category | Potential Impact | Primary Mitigation Strategy |
|---|---|---|
Smart Contract | Total and irreversible loss of funds from an exploit. | Only use protocols with multiple, reputable security audits. |
Oracle | Inaccurate liquidations, protocol insolvency. | Check if the protocol uses robust, decentralized oracles like Chainlink. |
Liquidity | Inability to exit positions, cascading liquidations. | Monitor pool depth and trade volume; avoid thinly traded assets. |
Governance | Treasury theft, malicious protocol changes. | Review token distribution; watch for concentrated ownership. |
MEV | Poor trade execution (slippage), front-running. | Use MEV-protection services or trade on DEXs with built-in defenses. |
Understanding this full spectrum of threats is the first step. Once you can see the dangers clearly, you can start building a real framework for on-chain risk management and shift from being a passive participant to an active defender of your capital.
How to Spot Red Flags with On-Chain Data
In DeFi, being a passive investor is a recipe for disaster. Your best defense is to be an active monitor. This means learning to read on-chain data not as a stream of random numbers, but as an early warning system protecting your capital. By tracking a few key metrics, you can go from being a passive user to an informed analyst who sees trouble coming long before it hits.
This active approach to on-chain risk management is non-negotiable in a space where threats are constantly evolving. Crypto's history is littered with examples, from off-chain disasters like FTX causing on-chain collapses to far more sophisticated exploits. Today, it's estimated that only 8% of DeFi protocols have what they consider full risk control, which puts the burden of vigilance squarely on you, the user. Luckily, the tools for monitoring have gotten much better, letting us make smarter, data-driven moves.
Total Value Locked (TVL) Instability
One of the quickest health checks for any protocol is its Total Value Locked (TVL). This number just represents the total amount of user funds locked in the protocol's smart contracts. While a steady climb in TVL usually signals growing trust, a sudden, sharp drop is a massive red flag.
A serious TVL decline can point to a few critical problems:
A Potential Exploit: Hackers could be actively draining funds right now.
Loss of Confidence: Large investors, or "whales," might be pulling out their cash due to bad rumors, a known vulnerability, or just a better yield popping up elsewhere.
Underlying Asset Volatility: If the TVL is mostly held in a volatile asset that just crashed, the dollar value of everything locked up will nosedive with it.
A healthy protocol has a stable or steadily growing TVL. Treat any unexpected, double-digit percentage drop within a 24-hour period as a serious warning that demands an immediate look.
Unstable Collateralization and Price Deviations
For lending protocols and stablecoins, collateralization is everything. It’s the core mechanism ensuring every dollar borrowed or minted is backed by enough assets to keep it sound. When these ratios get shaky or the price feeds that power them go haywire, the whole system is put on notice.
A key part of on-chain risk management is keeping an eye on a protocol's collateralization ratio. If this number falls below the required threshold, it can set off a domino effect of liquidations, creating huge market instability. At the same time, watch the oracle price feeds. A major difference between an oracle's reported price and the market price on major exchanges could be a sign of an oracle manipulation attack in progress. For a better handle on the methods used to spot this kind of trouble, diving into in-depth on-chain analysis can be a huge help.
Dwindling Liquidity and Suspicious Governance
Liquidity is the lifeblood of DeFi. Without it, you can't trade assets or get out of your positions without taking a big price hit—a concept known as slippage. Monitoring the depth of liquidity pools is crucial. A pool that’s shrinking fast makes a protocol an easy target for price manipulation and can literally trap users in their positions. For a deeper dive on this, check out our guide on how to manage common liquidity pool risks.
Finally, don't sleep on governance activity. Watch out for weird proposals, especially ones that show up out of nowhere with no community discussion. Red flags include proposals to change critical protocol rules, mint a massive amount of new tokens, or anything being pushed through by just a handful of wallets that control most of the voting power. This could be the first step in a hostile takeover of the protocol's treasury.
Right, you know the dangers out there in DeFi. But knowing isn't enough—you have to actively defend your capital. This is where on-chain risk management gets real. It’s about building a concrete plan of action, your own defensive playbook that turns theory into a workflow that actually preserves your money.
Forget finding one magic solution. The key is to layer your defenses to build a portfolio that can actually handle the chaos of DeFi.
Think of it like building a medieval castle. You wouldn't just throw up one big wall and hope for the best. You'd dig a moat, install a drawbridge, build reinforced towers, and then have an inner wall. Each layer is designed to stop a specific type of attack. Your DeFi strategy needs that same multi-layered thinking to be truly safe.
Diversify and Prioritize Wisely
First rule of the playbook: never put all your eggs in one basket. This old-school advice is even more critical in DeFi, where a single point of failure can mean losing everything.
Protocol Diversification: Spread your capital across a few different, independent DeFi protocols. If one platform gets hit with an exploit or an oracle goes down, the damage is contained instead of wiping you out completely.
Chain Diversification: Take it a step further. Deploy assets on different blockchains, like Ethereum, Base, and Solana. This move insulates you from chain-specific drama like network outages, bridge hacks, or insane gas fees that can trap your funds.
Beyond just spreading things out, you need to get good at spotting protocols with security baked into their DNA. Look for platforms that have features built to protect users from sudden, sketchy changes. One of the biggest tells is a timelock.
A timelock forces a mandatory delay between a governance vote passing and the new code actually being executed. This delay is your window of opportunity—it gives you time to exit if you see a proposal that looks shady or harmful.
A protocol without a timelock is like a bank letting a single manager change the vault code instantly with zero oversight. It’s a huge red flag for centralized control and a major governance risk.
Create a Pre-Deployment Checklist
Before you deposit a single dollar into a new protocol, you need to run it through a standardized checklist. This isn't about being bureaucratic; it's a disciplined process that forces you to look past the shiny APYs and check the fundamentals. A solid checklist is your first and most important line of defense.
Your pre-deployment audit should hit several key areas to build a full risk profile on any new opportunity. This is where practical on-chain risk management really begins.
Essential Vetting Checklist
Security Audits: Has the protocol been audited by multiple reputable security firms? A single audit doesn't cut it anymore. Look for two or more from well-known shops. Actually read the reports to see what vulnerabilities they found and if the team fixed them.
Team Transparency: Is the team public and doxxed, or are they a bunch of anonymous accounts? While an anon team isn't automatically bad, a public team with a proven track record adds a crucial layer of accountability.
Tokenomics Review: Dig into the governance token distribution. Does the team or a handful of whale wallets hold a massive percentage? This kind of concentration is a ticking time bomb for governance risk, where a few insiders can push through any proposal they want.
Community Health: Is there an active and engaged community on Discord or Twitter? A lively community often acts as an informal watchdog, spotting issues and keeping the team honest. If their socials are a ghost town, that’s a bad sign.
Hedging with Decentralized Insurance
Look, even with the best prep in the world, a catastrophic smart contract failure can still happen. To protect yourself from these black swan events, consider using decentralized insurance protocols. These platforms let you buy coverage on a specific protocol for a set period.
For a relatively small premium, you can get a policy that pays out if the covered protocol suffers a specific kind of loss, like a smart contract exploit. It's a direct financial hedge against the worst technical risks in DeFi. While it’s no substitute for doing your homework, it adds a final, powerful layer to your defensive playbook—a safety net for when the worst-case scenario becomes reality.
Automating Your Risk Strategy with AI

Trying to monitor DeFi risks manually is like trying to catch raindrops in a hurricane. The market never sleeps, exploits are launched by high-speed bots, and the critical data you need is scattered across thousands of contracts and countless transactions.
Even the most dedicated analyst simply can’t keep up. This gap is where serious risks fester, often going completely unnoticed until it's way too late.
This is where the next frontier of on-chain risk management kicks in: AI-powered platforms. These systems are built to drink from the firehose of on-chain data in real time, transforming a chaotic flood of information into clear, actionable signals. They don't just speed up the manual checks you’re already doing; they add a layer of predictive defense that’s impossible for a human to match.
Instead of you having to constantly refresh TVL charts or track whale wallets, an AI system does it nonstop. It learns a protocol's normal heartbeat so it can instantly flag when something is off.
From Reactive Defense to Proactive Protection
The big shift AI brings to the table is moving from a reactive to a proactive game plan. Manual risk management is almost always about damage control after a problem has already started. An AI-driven approach, on the other hand, is all about spotting trouble before it fully blows up.
Think of it as the difference between a smoke detector and a fire prevention system. A smoke detector is essential, but it only goes off after a fire has started. An AI-powered system is more like an inspector that's constantly checking for faulty wiring, gas leaks, and flammable materials—flagging risks to stop the fire from ever happening.
This is exactly what platforms like Yield Seeker operationalize for your capital. They connect all the dots we've talked about—smart contract bugs, oracle deviations, liquidity crunches, and governance attacks—into a single, intelligent engine.
Here’s a glimpse of how this automated protection works in the real world:
Real-Time Vulnerability Scanning: AI models can continuously scan connected smart contracts, looking for newly discovered exploits or suspicious function calls that don't match normal behavior.
Predictive Analytics: By crunching historical price data and oracle performance, these systems can actually predict the likelihood of a depeg or an oracle failure, especially during crazy market volatility.
Automated Liquidation Alerts: The system keeps an eye on your collateralization ratios across different lending protocols. It'll ping you long before you're in the danger zone, giving you precious time to add collateral or pay down debt.
This level of oversight turns on-chain risk management from a stressful, all-consuming chore into a background process that protects your assets 24/7.
An AI Dashboard in Action
Let's make this less abstract. Imagine you’re using a platform like Yield Seeker and its AI dashboard flashes an alert. This isn't just some generic warning; it’s a specific, contextual insight you would have spent hours digging for yourself.
The screenshot below gives you an idea of how a platform can visualize multiple risk vectors, translating raw on-chain data into a simple, easy-to-read risk score.
This dashboard might highlight a critical governance proposal in one of your protocols and simultaneously flag an unusual concentration of voting power among three brand-new wallets—a classic sign of a potential hostile takeover.
At the same time, it could detect that the primary oracle for a stablecoin in your portfolio is showing a tiny but persistent drift from prices on major exchanges. This is often the earliest indicator of a potential depeg. Catching these signals manually would require endless vigilance and deep expertise. With AI, these insights just show up. You can learn more about how to vet different automated risk assessment tools in our complete guide.
By pulling all these capabilities together, AI doesn't just make on-chain risk management easier; it makes it smarter. It provides the kind of institutional-grade protection needed to navigate DeFi's complex and often treacherous waters with real confidence.
Building Your Personal Incident Response Plan
Even with the best defensive playbook, a smart attacker can sometimes find a way in. In DeFi, the difference between a minor setback and a complete disaster often boils down to one simple thing: having a response planned out ahead of time. This is where your personal incident response plan—a crucial part of on-chain risk management—becomes your most valuable tool.
When a crisis hits, your adrenaline goes through the roof and clear thinking flies out the window. An incident response plan is your calm, rational guide, written by you when you were level-headed. Think of it as a step-by-step checklist to help you minimize the damage, stay focused under immense pressure, and avoid making a bad situation even worse.
Immediate Damage Control Steps
The moment you suspect a protocol you're invested in has been exploited, the clock starts ticking. Every second counts, and your first moves are absolutely critical to containing the blast radius. Your plan must prioritize cutting off your assets from the compromised protocol immediately.
Your emergency checklist should include these non-negotiable actions:
Revoke All Approvals: First thing's first. Go to a token approval checker and immediately revoke any permissions the compromised protocol has to access your wallet. This is like slamming a vault door shut on an intruder.
Move Funds to a Secure Wallet: Any assets not stuck in the protocol need to be moved to a clean, secure "cold" wallet. Pick one that has never interacted with the compromised platform. This quarantines your remaining capital from any further risk.
Unwind Related Positions: Do you have any related positions on other protocols? For example, are you using a liquidity pool token as collateral somewhere else? Unwind those positions right away to stop a domino effect of cascading liquidations.
Having these steps written down and the tools bookmarked before an incident is the whole point. Fumbling for the right website during a live exploit is a recipe for disaster.
Post-Incident Protocol and Learning
Once you've secured what's left of your assets, the next phase of your plan kicks in. This part is all about gathering information, documenting what happened, and most importantly, learning from it to make your future on-chain risk management strategy stronger.
You'll need to monitor official communication channels from the project's team—think verified Twitter and Discord accounts. Be extremely careful of scammers who will inevitably create fake accounts to post malicious links.
Next, carefully document your losses. Grab the transaction hashes, wallet addresses, and timestamps. This information can be vital if there's any chance of an insurance claim or a future recovery effort.
Finally, do your own personal post-mortem. Analyze what went wrong, what signals you might have missed, and how you can avoid similar risks in the future. Every painful lesson is an opportunity to get smarter for the next time.
Got Questions? We've Got Answers.
Jumping from theory to practice in on-chain risk management can bring up a lot of questions. Let's tackle some of the most common ones to make sure you're ready to protect your capital in DeFi.
What's the Single Biggest Risk for a DeFi Beginner?
If you’re just starting out, your number one focus should be Smart Contract Risk. Hands down. A single bug or backdoor in a protocol's code can mean a total, irreversible loss of everyone's funds. It happens more than you think.
Always, and I mean always, stick with protocols that have multiple, well-respected security audits and a long history of operating without a hitch. A golden rule for anyone dipping their toes in is to never invest more than you’re truly willing to lose, especially when it comes to newer, less battle-tested projects.
How Do I Actually Protect Myself from Oracle Hacks?
Dodging oracle manipulation really comes down to being picky about the protocols you use. You want platforms that are hooked into robust, decentralized oracle networks like Chainlink. Just as important, double-check that they aren’t relying on a single, thinly-traded market for their price feeds—that’s a classic recipe for disaster.
A simple but powerful move is to spread your positions across different platforms that use totally separate oracle providers. That way, if one oracle network gets attacked or fails, it won’t take down your entire portfolio. You contain the blast radius.
Is This On-Chain Risk Stuff Just for Big Institutions?
Not a chance. While the big trading firms definitely have their fancy, expensive tools, the core ideas of on-chain risk management are vital for every single person in DeFi, no matter how much you’re working with.
You can apply these exact same concepts right now by:
Spreading your assets across a few different protocols and chains.
Doing your homework on new projects before you deposit a single dollar.
Keeping an eye on public risk dashboards to monitor your positions.
Having your own simple plan for what to do if things go wrong.
The strategies we've walked through are built to be flexible, giving you a solid framework that works for any size portfolio.
Ready to put your defense on autopilot and earn smarter yield? Yield Seeker uses AI to monitor these on-chain risks 24/7, moving your stablecoins to competitive, risk-vetted opportunities in real time. Get started with Yield Seeker today.